Discover Ingenious Safety with BQT Solutions for All Your Demands
Maximizing Service Defense: The Ultimate Guide to Electronic Security Solutions
In the busy and ever-evolving landscape of business protection, the reliance on electronic safety services has actually become paramount for safeguarding important assets, secret information, and maintaining functional connection. As dangers to businesses continue to grow in complexity and frequency, the requirement for an extensive and robust protection technique can not be downplayed. In this guide to digital safety and security solutions, we will certainly explore the most up to date patterns, innovative modern technologies, and ideal practices to fortify your company versus possible dangers and vulnerabilities. Remain ahead of the curve and make sure the defense of your business with our comprehensive examination of digital safety and security remedies.
Relevance of Electronic Security Solutions
When considering the protection of assets and sensitive info, the value of digital protection remedies can not be overstated. In today's interconnected world, where cyber dangers are continuously evolving and becoming much more advanced, organizations have to prioritize executing durable digital protection procedures to guard their data and procedures. Digital security services encompass a wide variety of technologies and methods developed to protect versus unauthorized access, data violations, malware, and other cyber risks.
Among the vital advantages of digital safety and security options is their ability to supply real-time monitoring and threat detection. BQT Biometrics Australia. With tools like invasion detection systems, firewall programs, and safety and security info and occasion management (SIEM) systems, organizations can proactively determine and react to safety and security cases before they escalate right into significant breaches. Furthermore, digital security options aid make sure conformity with industry guidelines and criteria, shielding organizations from possible legal and monetary repercussions
Sorts Of Electronic Safety Equipments
Given the crucial relevance of digital security options in guarding businesses versus cyber dangers, it is important to discover the numerous kinds of digital safety systems offered to improve protection and strength. One of the most common types of digital protection systems is the firewall, which acts as an obstacle between a business's internal network and outside networks, filtering system out possibly hazardous information. By employing a mix of these digital security systems, businesses can establish a durable protection against numerous protection threats.
Executing Gain Access To Control Procedures
Additionally, access control procedures can be incorporated with security systems to check and tape-record people' movements within secured locations. This combination enhances security by providing a thorough summary of that is accessing details places at any given time. Accessibility control systems can be configured to limit access based on time, location, or individual qualifications, enabling organizations to personalize safety and security procedures according to their certain demands.
Cybersecurity Best Practices
To improve total safety stance, implementing durable cybersecurity best methods is vital in securing digital properties and information integrity. Performing regular safety and security audits and assessments helps identify weaknesses and areas for enhancement.
Establishing an extensive incident action plan enables swift and reliable feedbacks to safety breaches, decreasing possible damages. Carrying out gain access to controls based on the principle of least opportunity limits the direct exposure of important systems and details to only those that need it for their duties. By including these best techniques right into cybersecurity methods, businesses can fortify their defenses against evolving cyber hazards.
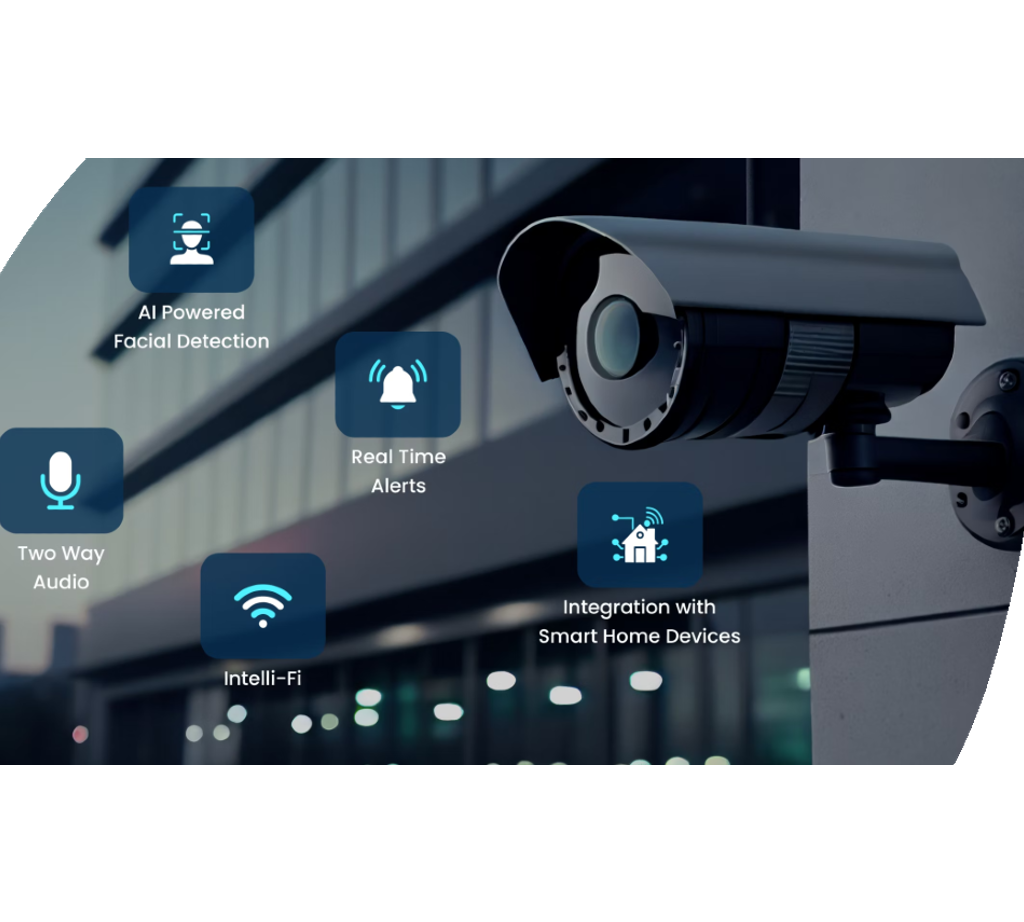
Surveillance and Monitoring Solutions

Video surveillance solutions supply remote monitoring capabilities, permitting authorized workers to keep an eye on the facilities even when off-site. In addition, advanced functions like motion detection, face acknowledgment, and permit plate acknowledgment improve the total security posture of the organization. index Incorporating monitoring systems with security system and gain access to control additionally strengthens the protection infrastructure, making it possible for a proactive response to potential protection breaches.
Conclusion
In verdict, digital protection options are important for making best use of organization protection. It is important to spend in the ideal electronic security systems to make certain the security and security of the organization.